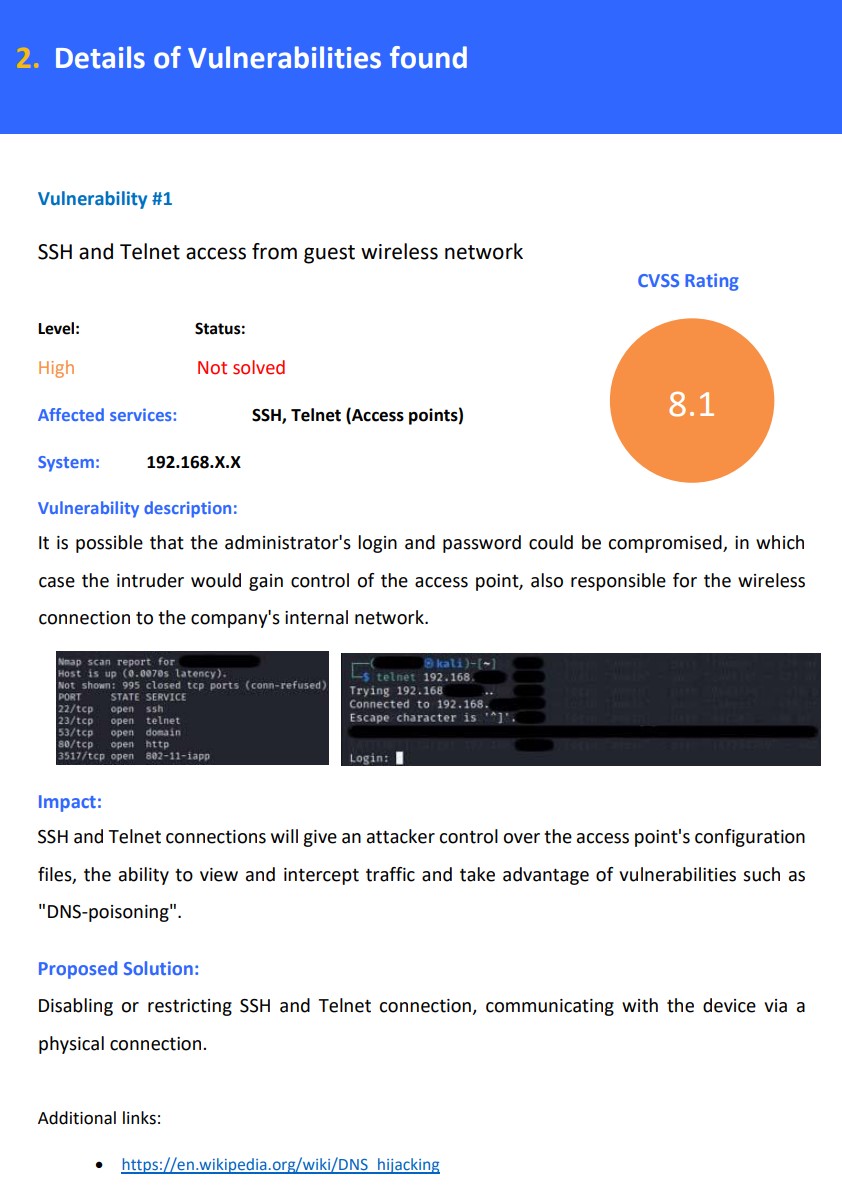
For enterprise security, I cannot show any real data, such as actual external and internal ip-addresses, as well as vulnerabilities found.
The company's network was tested, primarily the possibility of penetrating the network via Wi-Fi for both guests and internal employees.
Example of a page from a Security Audit Report